Computer Networking
Overview
The Computer Networking can be classified according to different standards.
In this book,we divided the system into five layers:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Application Layer
Meanwhile,the Computer Networking can be also divided into seven layers:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
We will describe the architecture according to the model with five layers above.
Application Layer
What is the Application Layer used for?
This layer is used to implement network applications.Obviously,those interesting network apps we using everyday is the reason why the whole computer networking exsits.
How to develop network apps?
For an application developer,the architecture of the computer networking is fixed.The whole system provides services to programmers for developing various applications.
So the very beginning thing the programmer should do is to design the architecture of the application(application architecture)
After that,he should consider how the processes in different end systems could communicate.
Then,he should choose the transportation services the computer networking provides.
How to design the Application architecture?
The term “application architecture” refers to how a programmer manage the application in different end systems.
There are two types of application architecture:
- client-server architecture
- P2P architecture
client-server architecture
In this situation,there are two types of end systems:
- client end systems
- server end systems
Normally,the client end systems get services that provided by server end systems:
We name those server end systems as the Server.You can consider the server as one or more computers.The server is always running and maintained by someone.
If Kelly wants to obtain the services provided,she can use a client end systems(like PC,laptop, and etc.) to connect to the server.
Examples of the client-server architecture include the Web mail apps,Social networking apps,Web searching engings and .etc.
P2P architecture
In P2P architecture,the applications don’t connect with each other via the server.They connect with each other directly.
That is to say,there will be no server and client end systems in this architecture.
How the processes in different end systems could communicate?
First of all,we should make clear the definition of process:We can usually consider a running application as a process.
The application in an end system uses a special application called socket to send messages to another application in another end system.
In C/C++ or Python,we can use the corresponding libraries to control the action of the socket.
But how the socket can find the destination end system and application of the message?We use IP to note the destination end system and use Port to note the destination application.
We conventionally use port 80 to identify the Web Server application and use port 25 for Mail Server application(process).
How many transportation services the computer networking provides and how to make choices?
Services of transport Layer
Services of transport Layer includes TCP and UDP.
We can choose these two services in transport Layer according to criterias below:
- reliable data transfer:a service can promise to deliver messages to the destination without loss,we will call it reliable
- throughput:the maximum flow the service can carry
- timing:messages will arrive the destination within a certain time
- security:as the liteal meaning suggests
And TCP and UDP can provide different services:
| Service Names | Services provided |
|---|---|
| TCP | reliable data transfer,service facing conection |
| UDP | not reliable data transfer |
Services of application Layer
Services of application Layer consists of various protocols.Among them,the most widely used are:
- HTTP
- SMTP
- DNS
- .etc
The relationship between services provided by two different layers:
| Transportatioin services provided in Application Layer | Corresponding transportatioin supported services in Transport Layer |
|---|---|
| HTTP | TCP |
| SMTP | TCP |
| FTP | TCP |
| Telnet | TCP |
| SIP | TCP,UDP |
| DNS | UDP |
| POP3 | TCP |
Those specific services provided by the application layer
We now have a general idea of the application layer.So it’s time for us to discover some most widely used application layer services to consolidate the concepts we have mentioned above.
HTTP
What is HTTP?
HTTP is the short for HyperText Transfer Protocol.It is used to transfer Web Pages.
But what are Web Pages?Web Pages are usually considered as a set of objects.We generally understand an object as a file.
How do we implement HTTP services?
We use two programmes to achieve this service:the client application and the server application.The client application send a HTTP request to the remote server when needed and the server application in the server send a HTTP response to the client.
The HTTP service use TCP to transfer.And as we mentioned before,the socket play the role of bridge in connections between HTTP and TCP.
HTTP protocol is a stateless protocol,that is to say,the server don’t remember who had send requests to it before.So if a client send duplicate requests,the server will send responses also duplicately to the client.
TCP three times handshakes and four times handshakes
…
Two different ways of TCP connection we can choose under HTTP
As we all know,when a client communicate with a server,the client will send one or more requests to the server.So one of the most important questions the programmers will consider is how should we deal with these requests.
One way is to deal them one by one,which means deal build a TCP connection each request.Another way is to deal all the requests using only one TCP connection.We call the former way as “non-persistent connection“ and another way as “persistent connection“.
By default,the HTTP use persistent connection,because the advantage of it is obvious.
Structure of HTTP message?
HTTP messages can be classified into two categories:HTTP request messageand HTTP response message
HTTP request message

A HTTP request message has following contents:
Get /index.html HTTP/1.1
Host: www.baidu.com
Connection: close
User-agent: Mozilla/5.0
Accept-language: frThe first line is called request line,and the lines after that are calledheader line.These two items are collectively refered to as message header
The request line has three field:
- method: Get,POST,HEAD,PUT,DELETE
- URL: /index.html
- version: HTTP/1.1
The header line contains multiple negotiable items.The example above has:
- Host
- Connection
- User-agent
- Accept-language
You can find that there are a huge data block after the message header called the message body.When we use POST method,we use message body to send data entered by the user.
HTTP response message
There is an example:
HTTP/1.l 200 OK
Connection : close
Date: Tue, 18 Aug 2015 15:44:04 GMT
Server : Apache/2.2.3 (CentOS)
Last-Modified: Tue, 18 Aug 2015 15:11:03 GMT
Content-Length: 6821
Content-Type: text/html
(HTML contents)The details of the message is easy to understand,you can easily find blogs about it online.So we won’t repeat it here.
What exactly the “cookie” is?
The cookie is used by companies to identify users.We normally consider it as some numbers and texts.
Web cache(proxy server)?
We use proxy server to release the stress of the server.When a client send a response to the server,this message will be send to the proxy server first.If the resource client asked for exists in the proxy server,the proxy server will send it to the client immediately.If the resource don’t exsits in the proxy server,the proxy server will send a request to the inital server to aquire the resource.After that, the proxy server will save a copy in it and send it to the client.
The most commonly used proxy server in real development is Nginx.
It is worth mentioning that by using proxy server,we can achieve CDN(Content Distribution Network).
But how to make sure copies in proxy server is the newest?
We use conditional GET methods to achieve this goal.
When a client send a request,the proxy server will send a check request(conditional Get methods) to the initial server to check whether the resources in itself is outdated.
SMTP
What is SMTP?
SMTP is short for Simple Mail Transfer Protocol:a protocol used to transfer e-mails.
The architecture of SMTP service?
SMTP service consists of three parts:
- user agent
- mail server
- SMTP protocol
A user use the user agent(like Apple Mail,Gmail,Netease Mail and .etc) to send and recieve emails.After a user sending an e-mail,the message will be transfered to mail server,and the mail server use SMTP protocol to send the message to the destination.
Email related protocol
There are two types of related protocol:
- Mail Send protocol,including SMTP
- Mail Access protocol,including POP3,IMAP,HTTP and so on
Mail send protocol is used to send messages to the client mail server.
Mail acces protocol is used to send messages to the client’s uset agent.
DNS
What is DNS?
DNS is short for Domain Name System,which is used to build a map between urls and IPs.
How does it work?
The structure of DNS servers will provide the answer.
There are three layers of servers in DNS services:
- root DNS server:provide links to the next layer
- TLD(Top-Level Domain) DNS server:anaysis the top field(.com .edu) in the url and provide links to the next layer
- authority DNS server:provide the IP the client asked for
A client connect to the root DNS server first, the root DNS server will send the IP of corresponding TLD DNS server to the client.
Then the client connect to this TLD DNS server,and the TLD DNS server will send the IP of the corressponding authority DNS server to the cilent.
And the authority DNS server will send the IP corresponding to the url to the client,and the service finish.
In practice, there will be another type of servers: local DNS server.It doesn’t belongs to any of three layers above.When a client send a request,the request go straightly to the local DNS server instead of the root DNS server.And the local DNS server will undertake the task of querying IP and send the IP back to the client.
We can find two different query modes above:
- recursive query:query the client send to the local DNS server,local DNS connect with the root DNS server,root DNS server connect with the TLD server,TLD server connect with the authority server.
- iterative query:query between the local DNS server and the root server or TLD server or the authority server.
How could it work faster?
Obviously,the operation mode above is not so efficient as we expected.So we can use DNS cache to solve this problem.
We save the relationship at each query for a period of time.And the DNS server will send responds back immediately to the client if requested data exists in the cache.
Structure of DNS message?
There are two types of DNS messages:
- request messages
- response messages
the structure of these two types of DNS messages is the same:
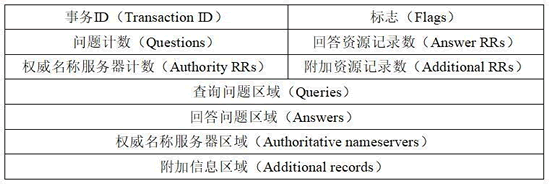
CDN
CDN is short for Content Distribution Network,it is widely used for distributing enormous data.
For example, a video website has a list of movies.A client wants to acquire a movie from the website,so it send a request message to the server of the website.The server won’t send the movie to the client immediately if the website uses CDN.In fact,the server will send a IP of a server which provide stroage services(usually belongs to a third party company) like the DNS system do.After several times of redirecting,the client builds a TCP connection with the server which saves that movie ans starts the process of transferring.
CDN has the cluster seletion strategy,which makes the data distribution easier and faster.
P2P
ellipsis
Socket programming
It has been recorded in another passage.
Transport Layer
The relationship between the transport layer and the network layer
The network layer provide corresponding services to the transport layer(usually IP services)
Multiplexing and Demultiplexing
Consider this sitiuation:a message of an e-mail and a message of a HTML document arrive an end system at the same time,how could this end system know which application should recieve which message?
We use multiplexing and demutiplexing to solve this problem.
| name | implication |
|---|---|
| Multiplexing | collect messages from different ports and send them to the transport layer |
| Demultiplexing | recieve mutiple messages from the transport layer and send them to the coresponding ports |
Implementation of UDP demultiplexing
In UDP service,we use a two-tuple to identify a UDP socket.Thus,a UDP message can use its destination port to locate the right socket.
Implementation of TCP demultiplexing
In TCP service,we use a four-tuple to identify a TCP socket.So only messages with the same origin IP ,origin port,destination IP and destination port will be send to the same port and processed by the same application.
UDP
| UDP’s features | explaination |
|---|---|
| without connection | UDP never connect to any UDP object before sending a message |
| UDP’s benifits:detailed control of transportation | There has the smallest restrains of transportation in UDP,so developers can control UDP easily |
| UDP’s benifits:without connection needs to be established | This makes the process of sending messages faster than TCP |
| non connection state | This make UDP can support more users because it is not as heavy as TCP |
| UDP’s benifits:tiny costs of message’s head | Only 20 bytes needed! |
| UDP’s disadvantage:unreliable transportation | In fact, it is possible to build a reliable protocol using UDP, but UDP itself is not reliable. |
UDP structure

TCP
Reliable Transportation Theory
basic Reliable Transportation protocols(SW)
| rtd version | background assumptions |
|---|---|
| rtd1.0 | completely reliable |
| rtd2.x | bit errors exist |
| rtd3.0 | bit errors and bit losses exsit |
(It is suggested to use the sequence diagram to explain these rtds because it is easier to understand.But for other motivation, FSM(Finite-State-Machine) is better)
pipelining reliable transportation protocols
Solve the problem of the time wasting in Stop and Wait Protocol(SW).
We can classify these protocols into two types(GBN/SR) by the way they deal with data missings.


